NssCTF round14
文章发布时间:
最后更新时间:
文章总字数:
预计阅读时间:
最后更新时间:
文章总字数:
1.2k
预计阅读时间:
6 分钟
love
这题可以非预期 但是由于时间比较充裕 就按照出题人的意思来做一做
比较简单的一题 难点在于最后的破坏了tls结构体的时候 不能选择system函数 要用syscall 但是稍微修复一下tls结构体 还是可以调用system函数的
考点在于pthread_create会使得新线程栈的布局迁移到tls结构体附近的一块地址 导致我们可以通过栈溢出覆盖到tls的canary 从而来绕过canary
修复tls结构体只需要把fs:0x10处的值覆盖成addr+0x308后是一个可读的地址即可
自己调一调就可以懂了
完整exp:
1 | from pwn import* |
rbp
劫持rbp可以任意写 然后就是打orw 没什么好说的
1 | from pwn import* |
xor
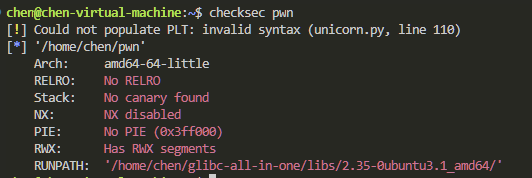
保护全关了 可用的攻击手法变得多元化起来了
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
程序的主体逻辑很简单
就是可以向一个任意地址 进行一次单字节的异或的操作
但是由于while循环的条件是flag小于等于0
执行完xorByteWithAddress函数后 flag的值自增 就退出while循环
所以我们首要的思路就是想办法把flag的值修改成负数
随后往bss段上写入shellcode 利用main函数结束会调用隐式exit函数 中间利用call函数调用了fini_array
通过覆盖fini_array就可以调用到shellcode
完整exp:
1 | from pwn import* |