Ciscn2023决赛
文章发布时间:
最后更新时间:
文章总字数:
预计阅读时间:
最后更新时间:
文章总字数:
801
预计阅读时间:
4 分钟
codelog
一道看起来是序列化的简单堆题。。。 被赛方开赛前说的有两题序列化protobuf跟flatbuffers坑了
导致先去看了第三题的正常堆 结果一个数独逆不出来。。。 结果爆零噜
1 | switch ( i ) |
主要的逻辑就是菜单 不过有几个函数起到了一个误导作用
关键的漏洞有两个 一个是init_code函数中存在了一个scanf引起的堆溢出 还有一个是没有开启PIE保护机制
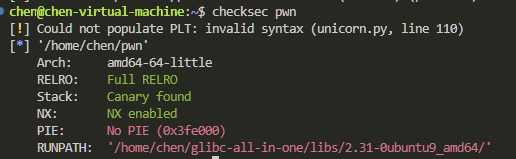
实际其他函数都是一个误导作用 我们只需要利用init_code函数的堆溢出 覆盖tcachebin的fd域 使得申请到bss段上 从而向存放chunk指针的数组写入got表的地址 这样就可以借助show函数把libc地址泄露出来了 随后利用同样的手法打free_hook
唯一要注意的就是init_code本身会对堆构造产生影响 所以需要自己动调注意一下
1 | from pwn import* |